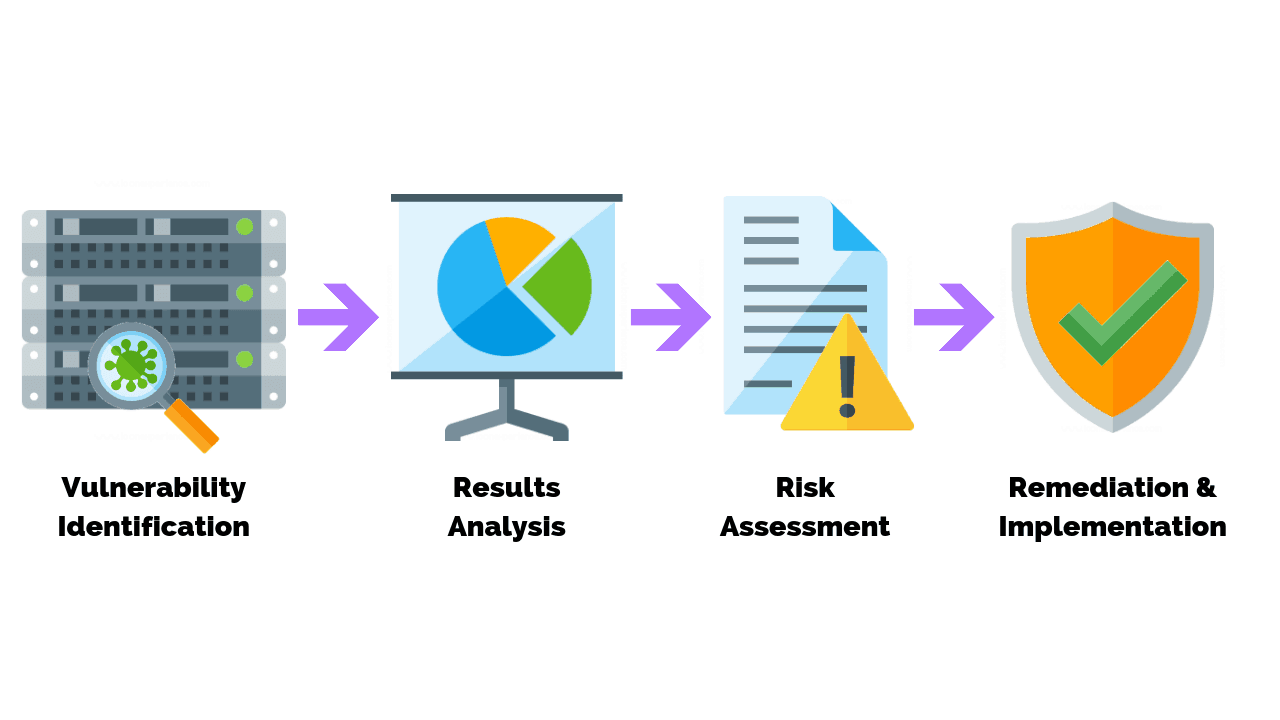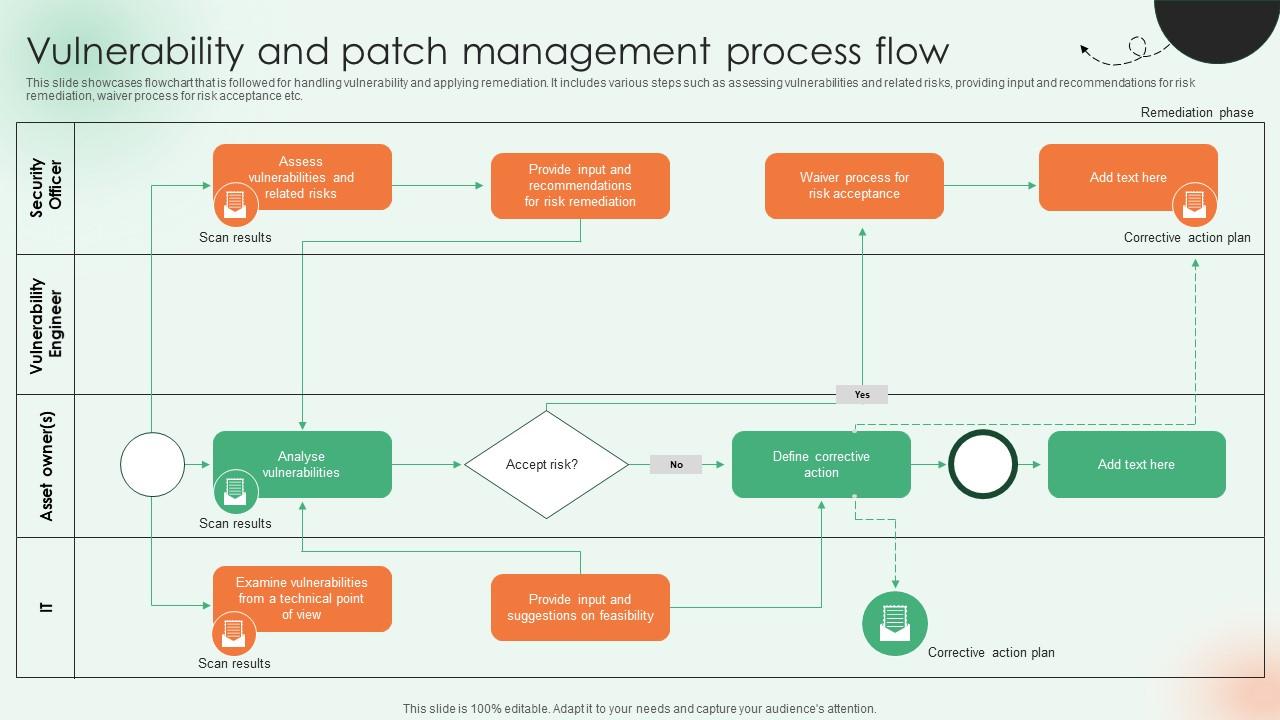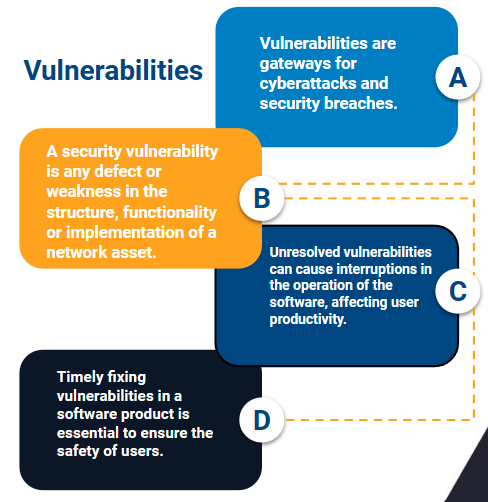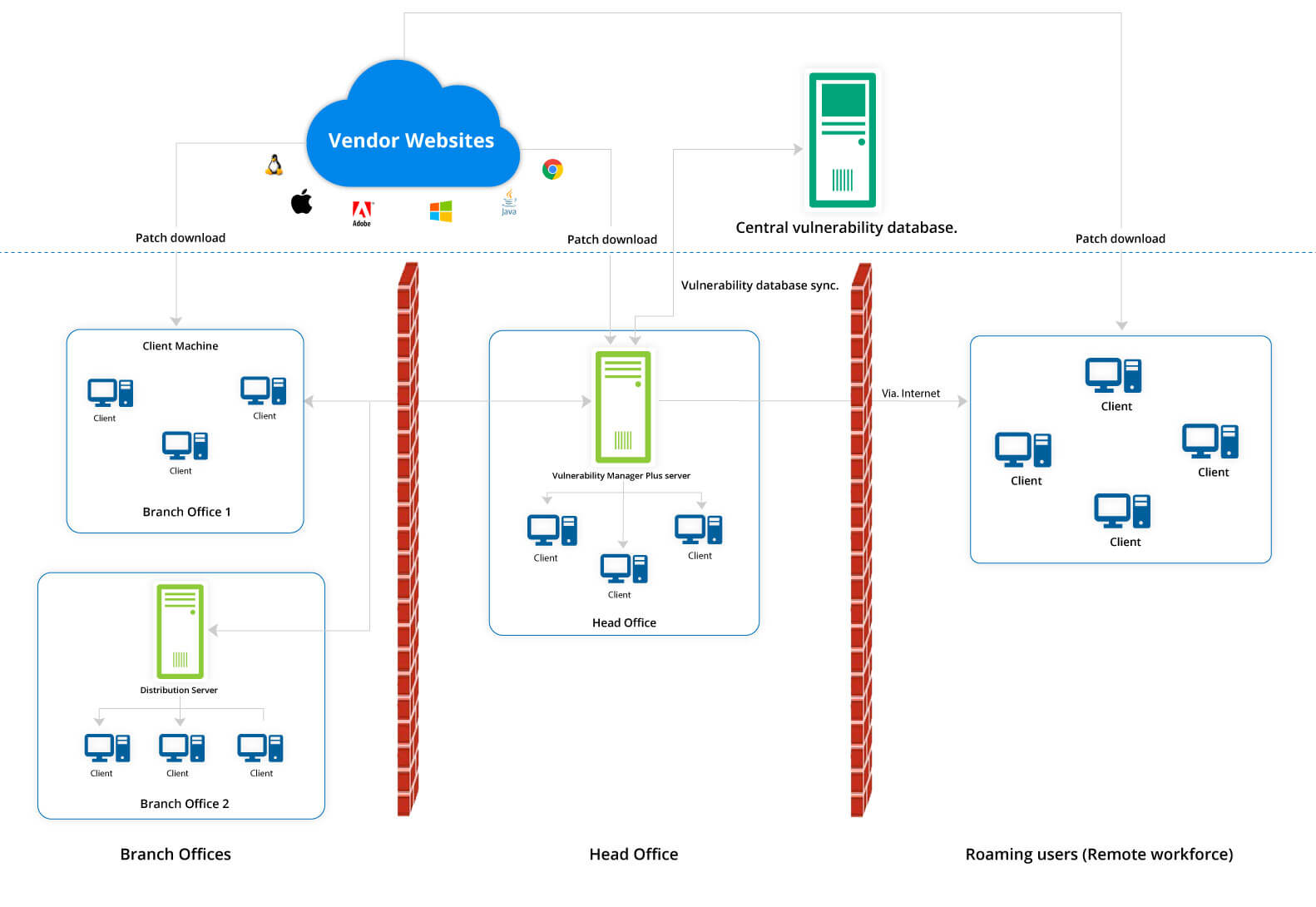
Définition de la gestion des vulnérabilités | Processus de gestion des vulnérabilités - ManageEngine Vulnerability Manager Plus
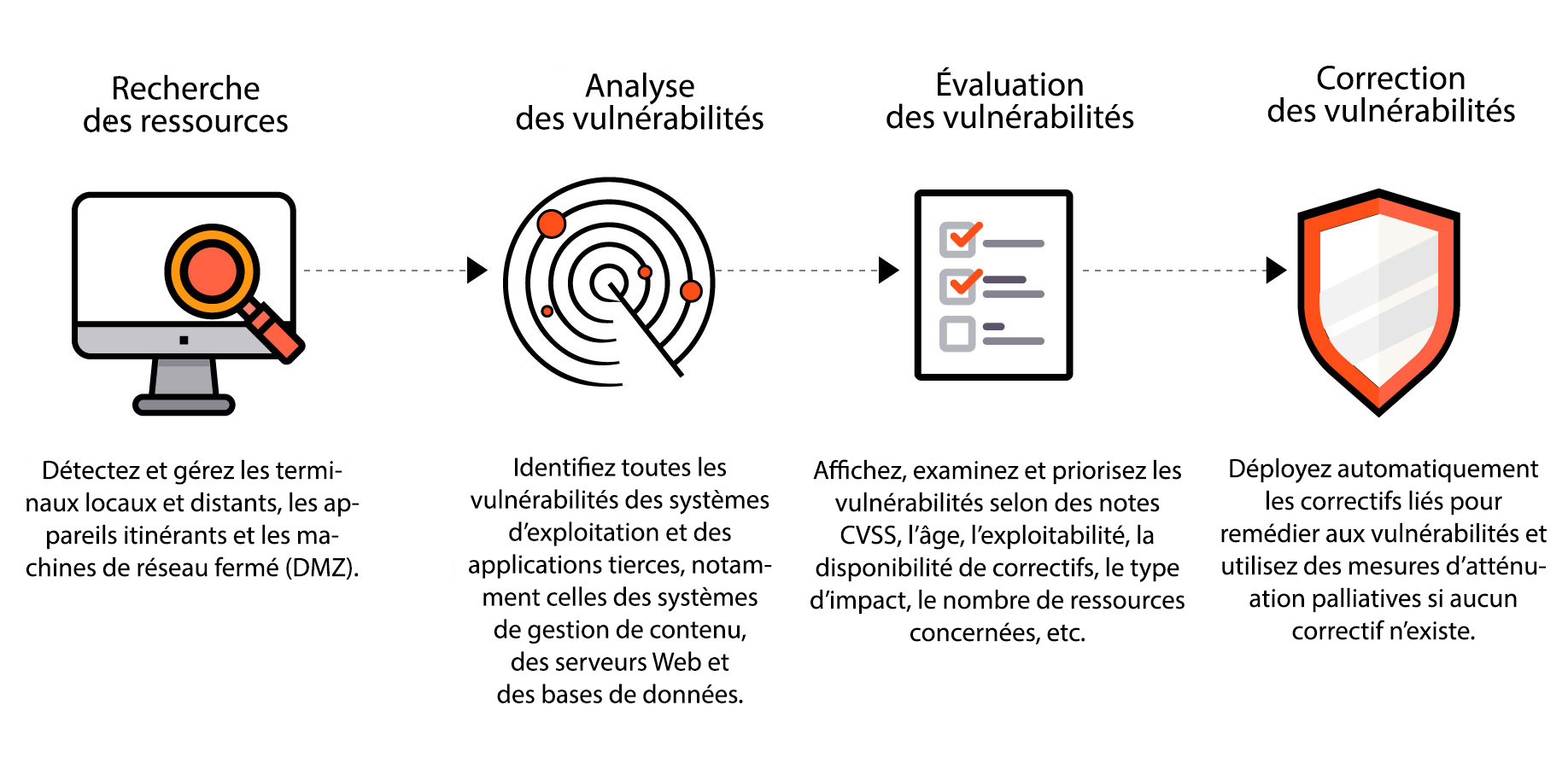
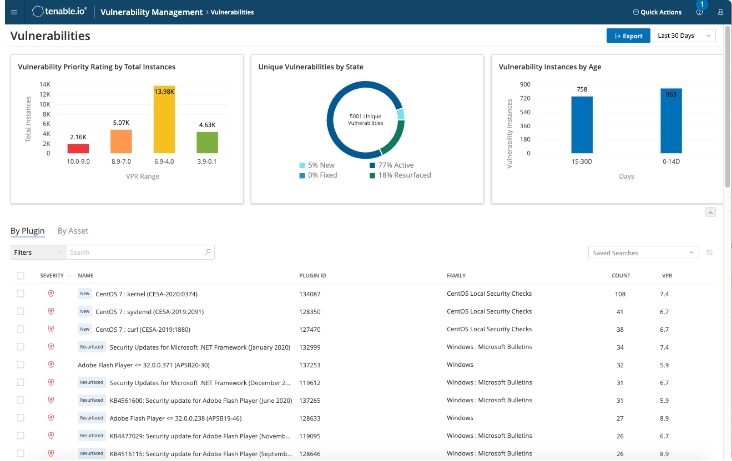
Analyse des vulnérabilités | Outil d'analyse des vulnérabilités - ManageEngine Vulnerability Manager Plus

A user-centred evaluation of DisCERN: Discovering counterfactuals for code vulnerability detection and correction - ScienceDirect
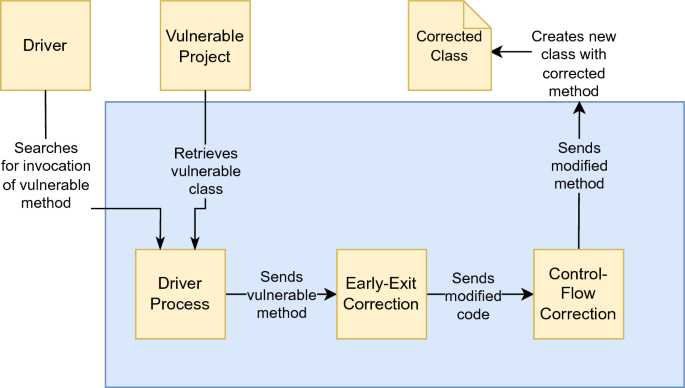
DifFuzzAR: automatic repair of timing side-channel vulnerabilities via refactoring | Automated Software Engineering

Fixing a security vulnerability in the system. Cyber security and corporate data protection. Error correction. Hacker attack. Malfunction, breakdown, out of order. Requiring a replacement. Stock Photo | Adobe Stock
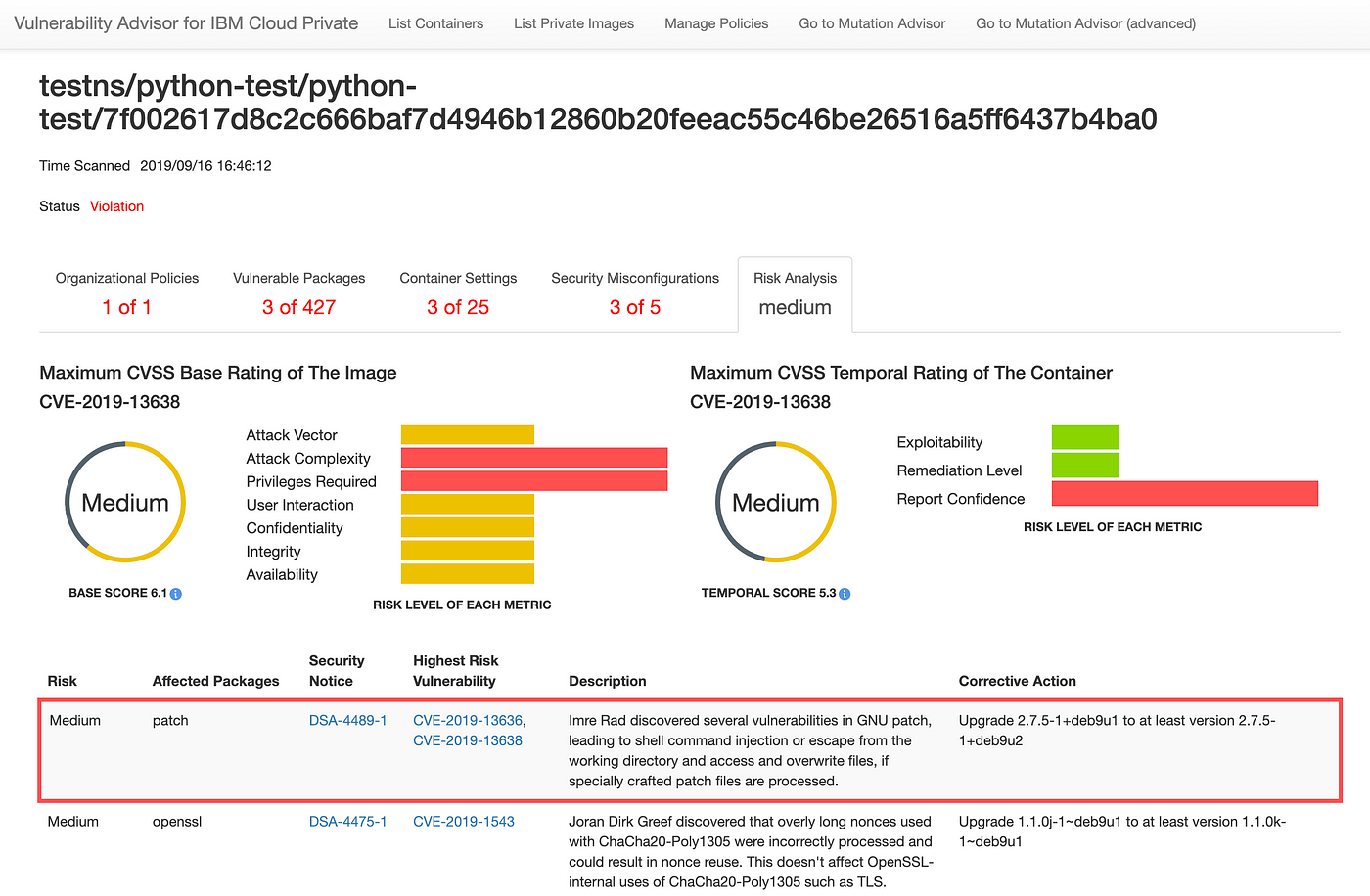
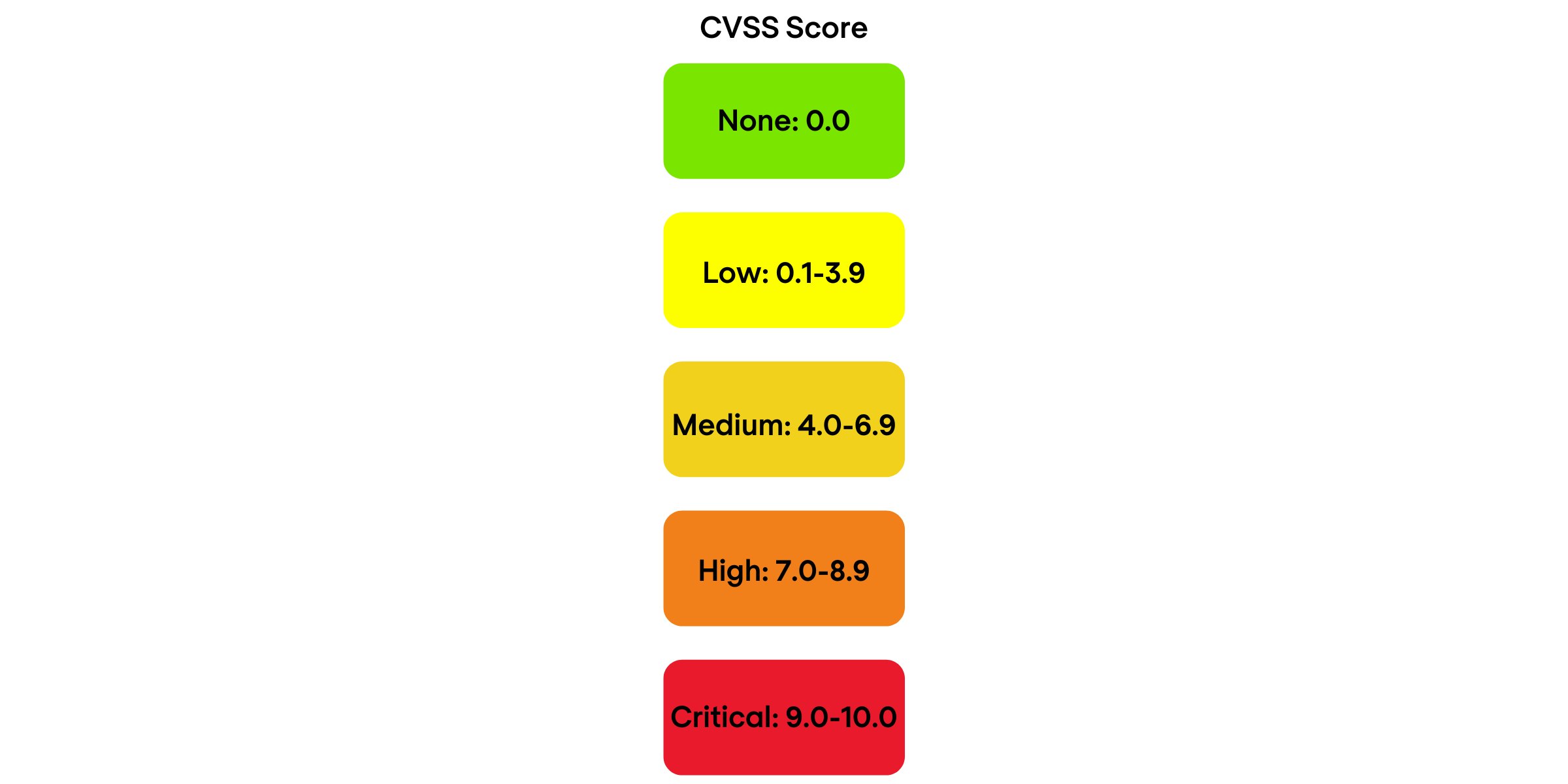
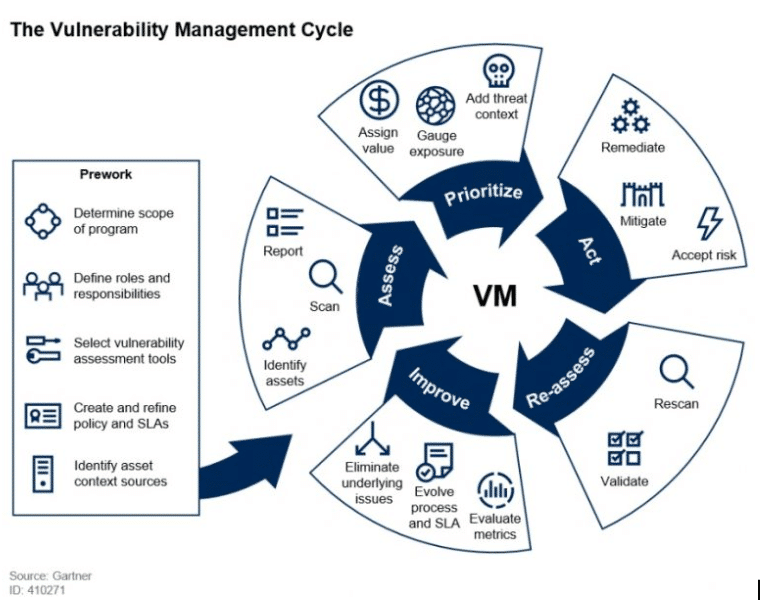
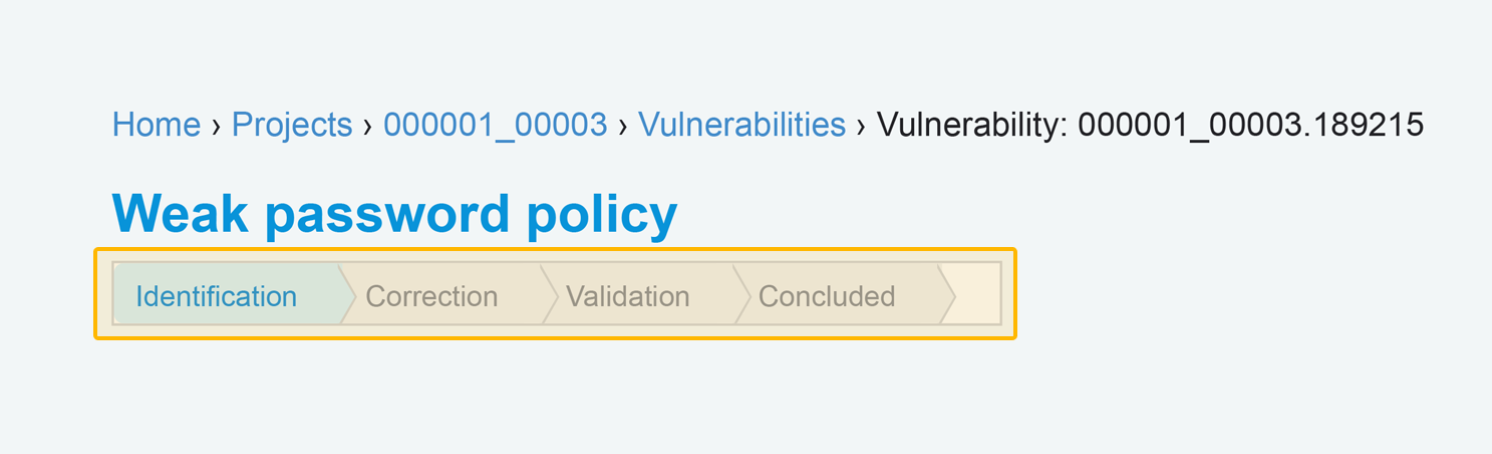
Assessing security risk of your containers with Vulnerability Advisor | by Yuji Watanabe | IBM Cloud | Medium